May 2013 Archives
2013-05-28
HTC's E-Mail Client Fails to verify Server Certificates
Severity: medium to high
Vendor: HTC
Products we known to be affected:
- Mail Version 5.2.2222282614.528614.528614 on an HTC One SV with Android 4.0.4, HTC Sense 4.1, HTC SDK API 4.25
- Mail Version 5.5.550363 running on an HTC One X with Android 4.1.1, HTC Sense 4+ HTC SDK API 4.63
Short Summary
modzero identified a vulnerability in HTC's default mail client. If the user chooses encrypted and authenticated communication to a mail server, the application does not verify the server's certificate and automatically accepts any certificate without asking or warning the user. Thus, an attacker is able to intercept a user's credential and e-mails, especially in rogue access point scenarios.Whole Story
While analyzing a wireless infrastructure, we were testing station behaviour regarding rogue access-points. Using airbase-ng and some metasploit capture server modules, the set-up was painless and straight forward.YEP, it works as expected; the phone connects to the rogue
network and tries to pull the e-mails from the SSL protected POP3
or IMAP servers. The iPhone did properly show a certificate
warning, because it could not verify the certificate while trying
to get the e-mails. Lets check how the other phones behave.
Booom - a username and password was captured!
Wait a second? SSL was enabled on all the configs right? Let's
check the config the HTC ONE X android phone again? YEP,SSL
enabled -maybe something is broken or someone had accept the
certificate already or ... whatever ... So we setup another fake
e-mail account and gave it a go.
Again, the password showed up and no certificate warning was
visible on the HTC ONE X e-mail client at all. This happens for POP
and IMAP accounts.
Great!Everyone can man-in-the-middle your apparently SSL
protected e-mail communication. FSCK ... impossible ...
Lets compare the available settings of a HTC Android phone and a
regular android phone:
| Other Android E-Mail Client | HTC E-Mail Client |
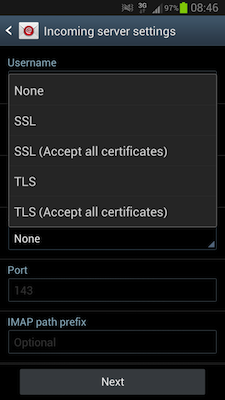 |
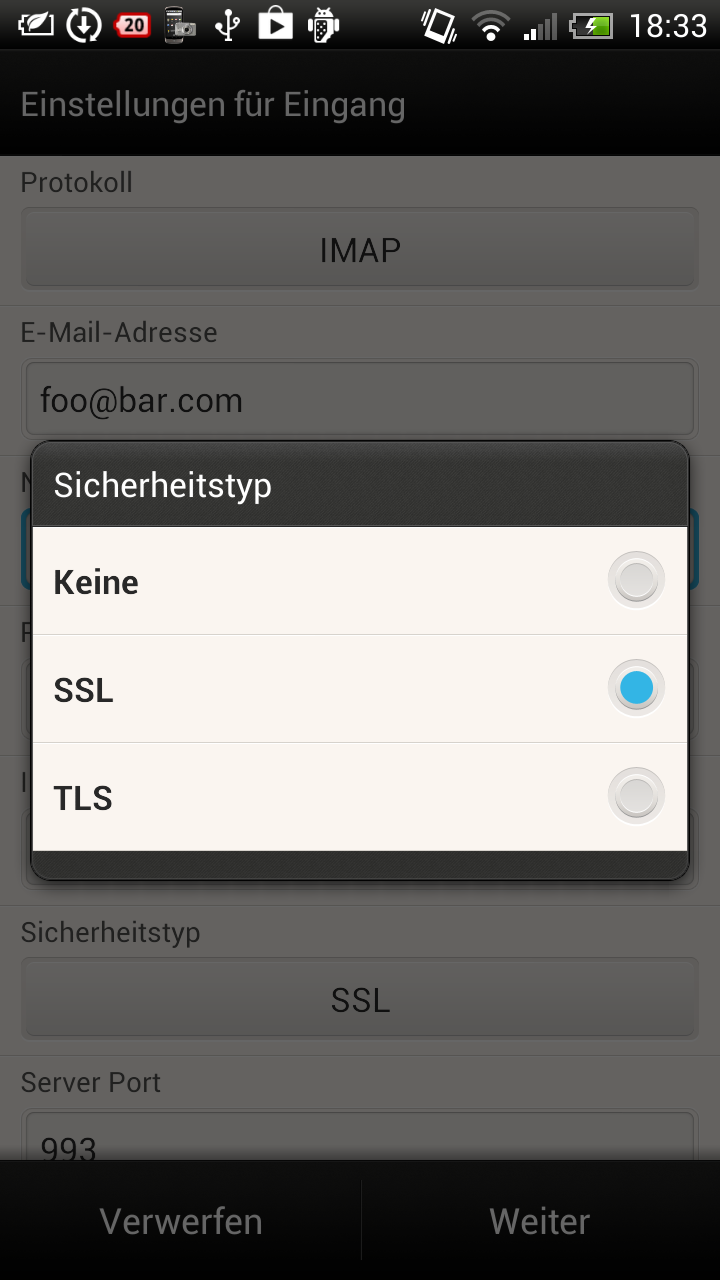 |
Did the guys at HTC wanted to make the user experience better? More options might just confuse their users? In fact the "SSL" setting on the HTC e-mail client does behave like the "SSL accept allcertificates" setting on other Android e-mail clients.
Using SSL is completely pointless, if you don't verify the
certificates at all.
We did not even bother to check what they precisely messed up in the E-Mail client code. HTC, please go and fix it. This is plain stupid. Other versions might be affected as well. Feel free to e-mail us regarding other affected versions.
Credits:
- Max Moser
- Martin Schobert
2013-05-15
Updates, Kraken & Conferences
News, Research, Talks & Trainings - A lot of new things happened in 2013. This is somehow the attempt to outline the most noteworthy stuff.
In February we hired Tobi! Tobias Ospelt was previously working
with our team as a freelancer, and we decided to contract him
directly. He focussed on software- and network-security and is
pretty good in breaking your networks :)
You can meet him on Thursday, May 16th 2013 at the Hacking Days Conference in
Zurich, Switzerland. Tobi is going to talk at the German speaking
Hacking Days in
Zurich about "Why IT people fail" covering the daily security
hassle for IT people and programmers.
The Internet-sealife's got a new life-form: Die Datenkrake. Thorsten Schroeder of
modzero and Dmitry Nedospasov of SecT
built a new toolchain for reverse-engineering and hacking hardware
& embedded devices. The project will be completely open source
and being launched in June 2013 during the REcon Conference in
Montreal, Canada. The idea behind the project is to utilize
programmable logic in conjunction with an ARM processor to analyse
and attack embedded systems and integrated circuits. All I/O wires
(there are eight channels with 6 I/O lines) are 5V tolerant
(bi-directional) and can be accessed directly via the FPGA. Dmitry
and Thorsten developed a 4-day practical training on hacking and
analysing hardware. The training will cover everything that is
necessary to utilize Die Datenkrake for hacking: Programming ARM
microcontrollers (C) and FPGAs (Verilog), logic & hardware 101,
passive and active attacks on hardware & busses, using
oscilloscopes and other instruments, strategies, etc. The training
will be launched at the REcon 2013 Conference in Montreal as well:
http://recon.cx/2013/trainingsynple.html.
However, we are planing to let this training happen again in
Germany and/or Switzerland at the end of 2013. Contact us, if you
are interessted in this training - we also do individual on-site
hands-on workshops for your teams.
- 16th May 2013 - Tobias Ospelt at Hacking Days Zurich, CH: Why IT people fail (more...)
- 23th May 2013 - Thorsten Schroeder and Dmitry Nedospasov at PHDays in Moscow, RU: Let the Hardware Do All the Work: Adding Programmable Logic to Your Toolbox (more...)
- 4th June 2013 - Thorsten Schroeder at Kedua Datenschutztag 2013 in Berlin, DE: Death by Comfort - Wenn Alltagsgegenstände zum Datenschutzproblem werden (more...)
- 17th June 2013 - Thorsten Schroeder and Dmitry Nedospasov at REcon 2013 Trainings in Montreal, CA: Keep It Synple Stupid: Utilizing Programmable Logic for Hardware Reverse-Engineering - a 4-day hands-on training session (more...)
- 21th June 2013 - Thorsten Schroeder and Dmitry Nedospasov at REcon 2013 Conference in Montreal, CA: Keep your tentacles off my bus, introducing Die Datenkrake (more...)
- 5th July 2013 - Thorsten Schroeder and Dmitry Nedospasov at SIGINT.CCC.DE in Cologne, DE: Benutze Krake mit Gerät (more...)
Last but not least: modzero now officially also got a German subsidiary - modzero GmbH. modzero GmbH Germany is a privatly held company, founded and owned by Max Moser and Thorsten Schroeder in early 2013 in Berlin.